Tutorials | Fern Wifi Cracker Tool for Hacking Wi-Fi Networks
In today’s world, Wi-Fi networks are essential for accessing the internet. However, these networks can sometimes be vulnerable to hacking by attackers using advanced tools like Fern Wifi Cracker.
We have previously explained the method of hacking Wi-Fi networks using the Airodump-ng tool. However, this tool relies on the command line, so you need to know the codes.
Unlike the Airodump-ng tool, Fern Wifi Cracker has a graphical user interface, making it relatively easier to use compared to the previous tool. This feature makes it very suitable for beginners in this field.
In this article, we will explain what Fern Wifi Cracker is and how it works, and provide tips on how to protect your Wi-Fi network from being hacked.
What is the : Fern Wifi Cracker tool?
Fern Wifi Cracker is a wireless security auditing and attack software written using the Python programming language and the open-source Python Qt GUI library.
The tool is capable of cracking and recovering WEP/WPA/WPS keys and also launching other network-based attacks on wireless or Ethernet-based networks.
Fern Wifi Cracker was developed by Savio Code, a well-known programmer and content creator in the Kali Linux community. No official team has been announced as contributing to the tool’s development, but Savio Code receives contributions from the Kali Linux community through the GitHub platform.
Fern-Wifi-Cracker is designed to be used for testing and discovering vulnerabilities in a person’s private network with the aim of fixing the discovered vulnerabilities.
Features of: Fern Wifi Cracker
– Ease of Use: It features a graphical user interface (GUI) that makes network penetration very easy, even for beginners.
– Integrated in Kali Linux: It comes integrated in the popular Kali Linux distribution, making it easily accessible and usable.
– Supports Multiple Attacks: It supports a variety of Wi-Fi penetration attacks, including WEP, WPS, and WPA/WPA2.
Requirements for: Fern Wifi Cracker
Operating System Requirements
- Linux: Fern Wifi Cracker requires a Linux operating system to run.
- Kali Linux: It is highly recommended to use Kali Linux, a Linux distribution specifically designed for penetration testing and security, because the tool is integrated into this distribution and runs smoothly on it.
Resource Requirements
- Processor: Intel Core i3 or newer.
- Wireless Network Adapter: A wireless network adapter compatible with 802.11 b/g/n/ac standards.

Notes:
- System requirements may vary slightly depending on the version of the tool and the Linux distribution used.
- Make sure to update your operating system and drivers before installing Fern Wifi Cracker.
- It is also important to have a properly functioning internet connection to use the tool fully.
Algunos sitios importantes
Official GitHub page for Fern Wifi Cracker: https://github.com/savio-code/fern-wifi-cracker
Kali Linux Documentation: https://www.kali.org/docs/
Kali Linux Forums: https://forums.kali.org/
Network Targeting Method: Steps of Penetration
Breaking into or bypassing the protection of a WiFi network is done through four stages, as follows:
1. Searching for the targeted network.
2. Selecting the targeted network.
3. Obtaining the handshake file for the targeted network.
4- Guess or crack the password of the target network.
Yes, these are the only four steps through which you can penetrate any network on the face of the earth, but the method is not that easy.
It’s true that the first two steps of searching and selecting the network are easy, but the difficulty lies in the third and fourth steps where you have to guess or predict the password.
Explanation of the third stage: Handshake File
It is a file used in network communications to exchange information between two devices when establishing a connection. This file typically contains identifying information about each device.
Such as the initial address (IP address), device identifier (MAC address), and supported connection settings. The handshake file helps establish a smooth and secure connection between devices on the network.
For example, when you connect your device to a new Wi-Fi network, a handshake file is sent to the Access Point that manages the network.

This file contains information such as your device’s IP address and its MAC address, allowing the network to verify its identity and grant access to it.
How to obtain this file?
This file can only be obtained through one method, which is to wait in monitoring mode until a device with the password logs into the network.
Okay, it seems waiting for someone to connect to the network is not practical and involves waiting for hours until someone logs in and obtaining this file.
Okay, what if I told you that there’s a way to kick everyone off the network, so they’ll try to reconnect again, allowing us to quickly obtain the file.
The Fern Wifi Cracker tool allows you to easily obtain this file by targeting the network and kicking everyone off it. Then, you wait for devices to reconnect, making it easy to obtain the handshake file.
Explanation of the fourth stage: Password Guessing
Guessing literally means trying to predict the password, such as manually testing passwords you think might be the network password. However, the factor of time is the reason this step often fails.
Therefore, we need tools that accelerate this guessing process. Fern Wifi Cracker can do that; after obtaining the handshake file, you can input millions of potential passwords into a file you create yourself.

And as previously explained, we discussed how to create a file containing your own passwords for use in targeting attempts, or selecting pre-existing files available in the Kali Linux system.
After creating your file containing passwords and then placing this file into the password guessing tool, you can subsequently attempt to break the protection of the targeted WiFi network.
Network Targeting Method: Using the Fern Wifi Cracker Tool
Firstly, it should be noted that using this tool for illegal purposes may subject you to legal consequences.
Note that if you encounter an error when enabling the monitoring mode of the tool, you should refer to our previous article where we explained how to resolve this issue.
1. Start by booting up Kali Linux. From the toolbar, search for “fern” and click on the tool to open it.
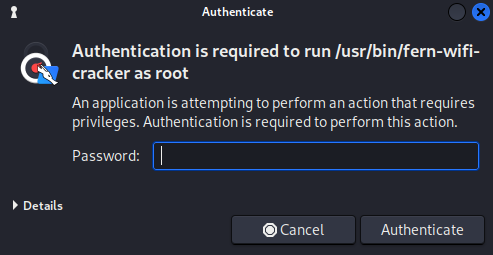
2. You will see a screen prompting you to enter the password to confirm that you are the system owner. The default password is usually “kali” if you have not changed it.
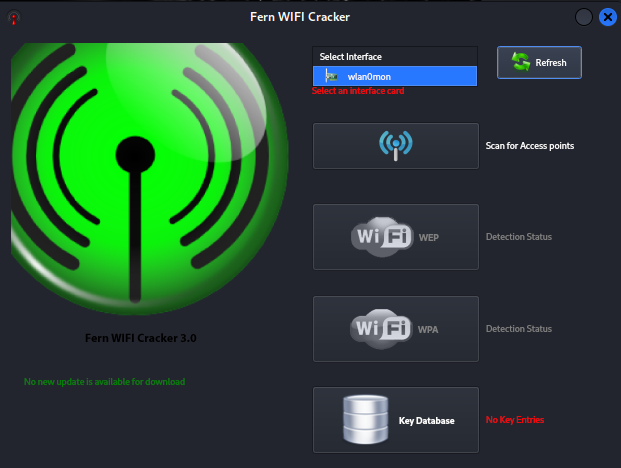
3. Now, by selecting the first option which is the adapter name, choose the modified name “wlan0mon“. If your adapter name is different, you can refer to the article here to change the name.
4. We switch the device to monitor mode using the second option. We wait until the word “Active” appears next to it in green color.
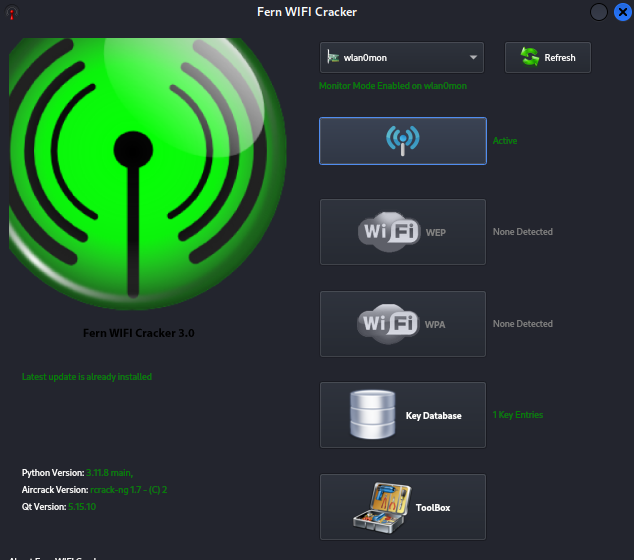
Now the tool is ready to target networks
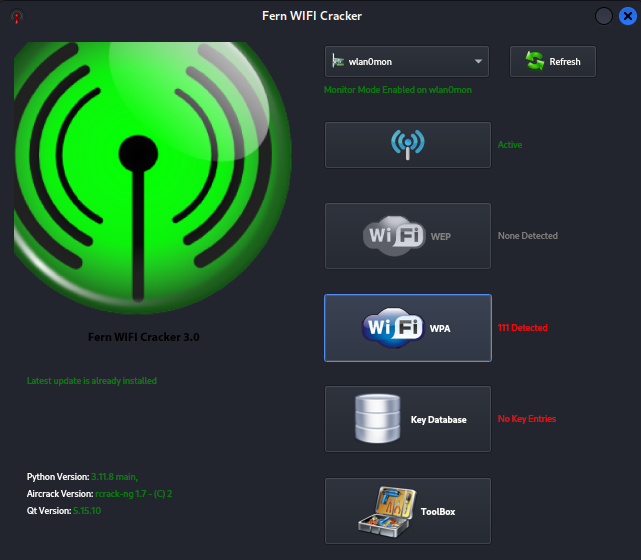
Now, as shown in the image above, the tool is ready to search for networks. All we have to do is choose the target network to crack the password.
5. Click on the fourth option, which is “wifi wpa,” to search for the targeted network.
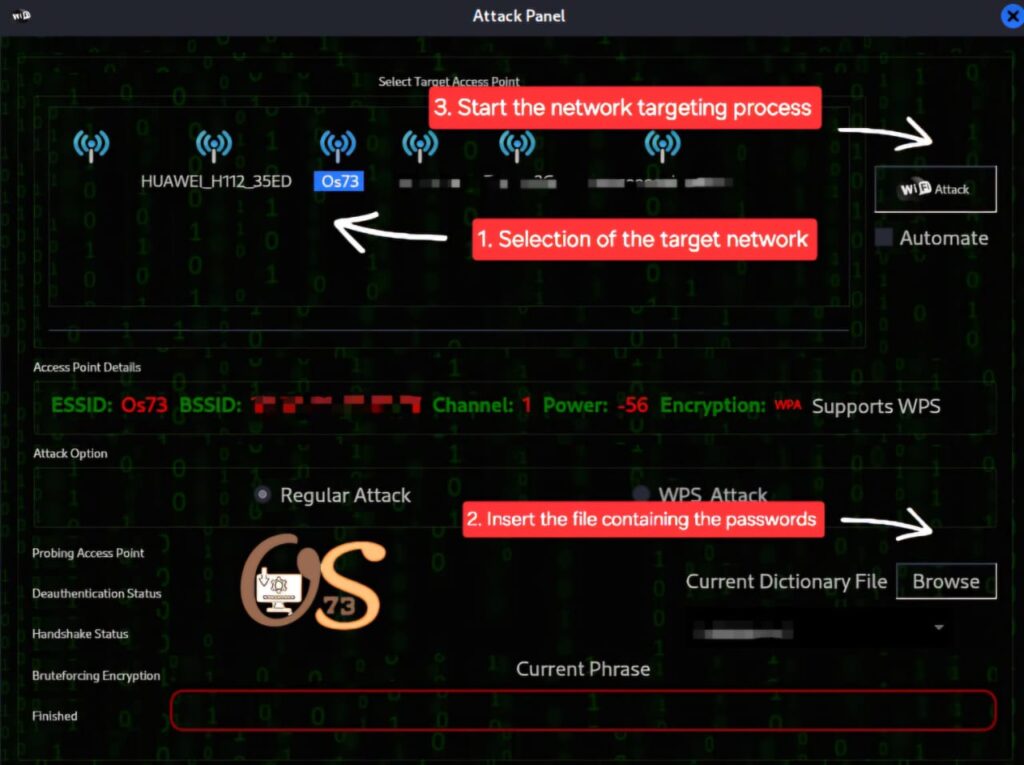
6. You will see another menu displaying nearby networks ready to be targeted. Choose “your network” then select the file containing the passwords (explained in step four above).
7- After clicking on the targeting word “wifi attack”, all you have to do is wait to obtain the password used.
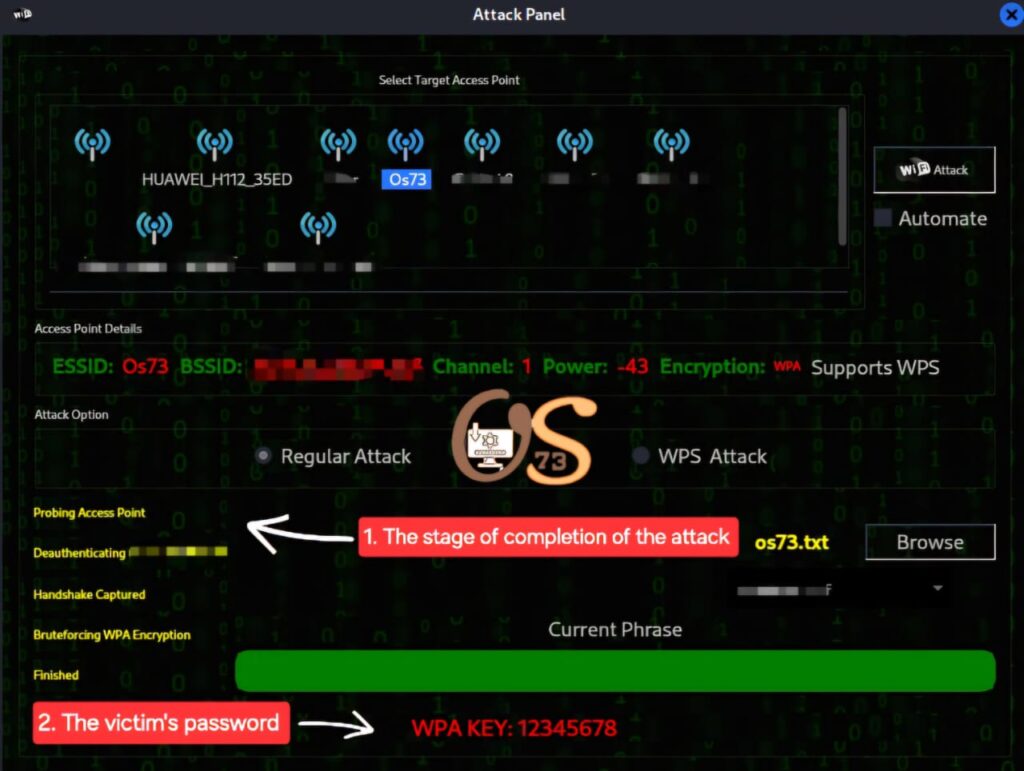
And as shown in the image above, the handshake file password has been obtained, which is “12345678“. Now you can use this code to connect to the targeted network.
End of explanation
This is how you can obtain the password for any network you wish. The method relies on the password file you create, containing passwords you anticipate the target might use.
Targeting will succeed, and through it, you can understand the attacker’s mindset. This allows you to set stronger and more unexpected passwords for your own network.
I hope I have successfully explained the Fern Wifi Cracker tool clearly and thoroughly. If you have any questions or issues, please feel free to let me know below.
