apps | Folder Widget: An App Organization Tool for Android Phones
Are you overwhelmed by app clutter on your phone screen? Looking for a way to organize them better and make them easier to access? Here’s the solution! The Folder Widget app.
Folder Widget app provides an ideal solution to this problem. It offers great capabilities for organizing your Android phone apps efficiently and easily, giving you a tidy and attractive phone screen that allows easy access to frequently used apps.
The app is a tool for organizing your apps on your Android phone, allowing you to place apps inside folders on the home screen.

you can : With the Folder Widget app
- Create custom folders to organize your apps by category or usage, such as “Social Media,” “Games,” or “Work.”
- Customize the appearance of folders by choosing icons, backgrounds, and colors that match your taste.
- Add shortcuts for the most frequently used apps inside the folders, saving you time and effort.
- Support adaptive icons for Android 12, giving your phone a more modern look.
- Enjoy ease of use with an intuitive interface that allows you to create and customize folders effortlessly.
- Experience a lightweight app that does not significantly impact your phone’s performance.
However, like any app, Folder Widget may have some drawbacks, such as:
- Ads: The app may include some ads that could be annoying to some users.
- Paid premium features: Some advanced features, like the ability to lock folders with a password, require purchasing the paid version of the app.
- Limited support for all app types: The app may not work correctly with certain types of apps, such as instant messaging apps.
Overall, Folder Widget is a valuable tool for organizing Android apps and significantly enhancing the user experience. Despite some minor drawbacks, it is worth trying, especially for users struggling with app clutter
Download the : Folder Widget application

| Application size: | 31.66 MB |
| APP COMPATIBILITY: | Supports all operating systems, including Android |
| License: | Free, and there is a possibility of purchase |
Application download link
How to : Use the Folder Widget App
Step One:
- Download and install the app from the link above.
- Tap on the home screen until the “Widgets icon” appears, then tap on it.
- Now, choose the style you prefer.
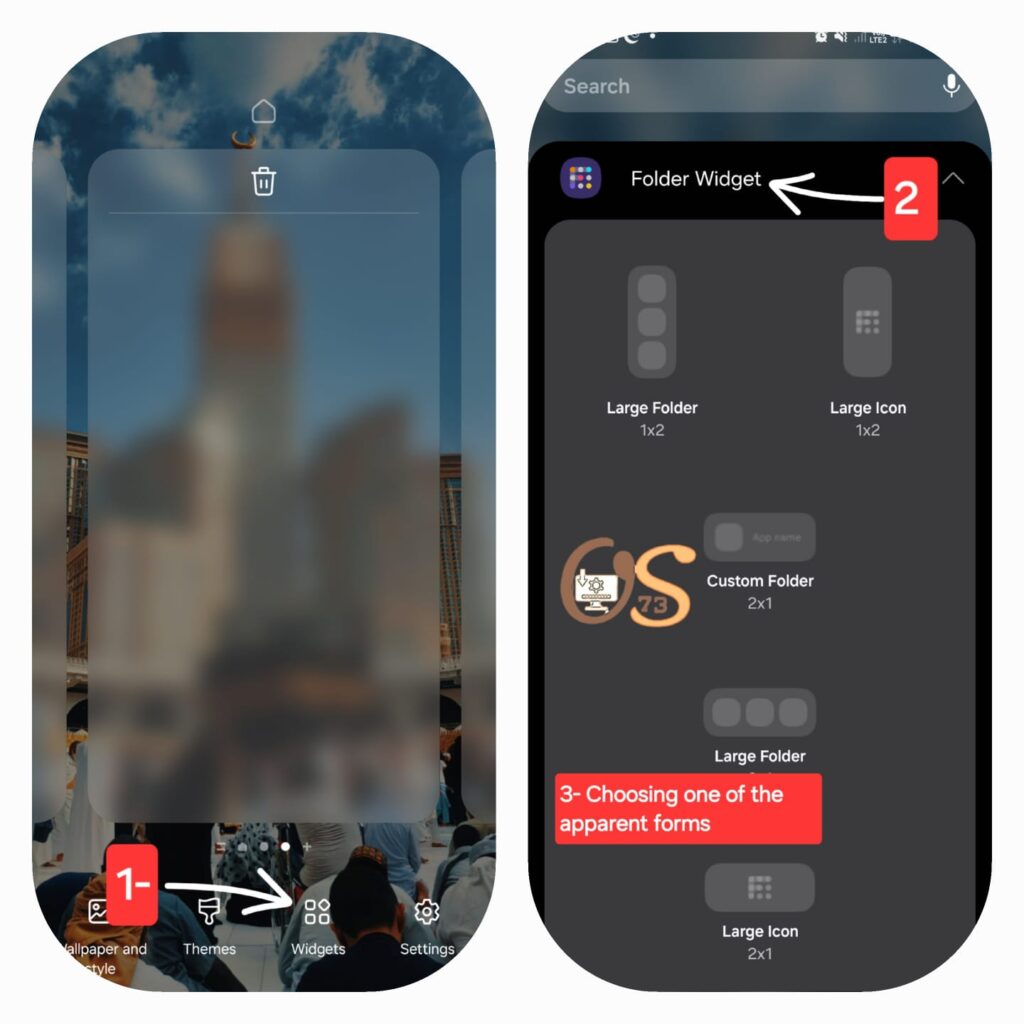
Step Two:
- Select the apps you want to place inside the folder you created.
- The folder will appear on the home screen with the apps you selected.
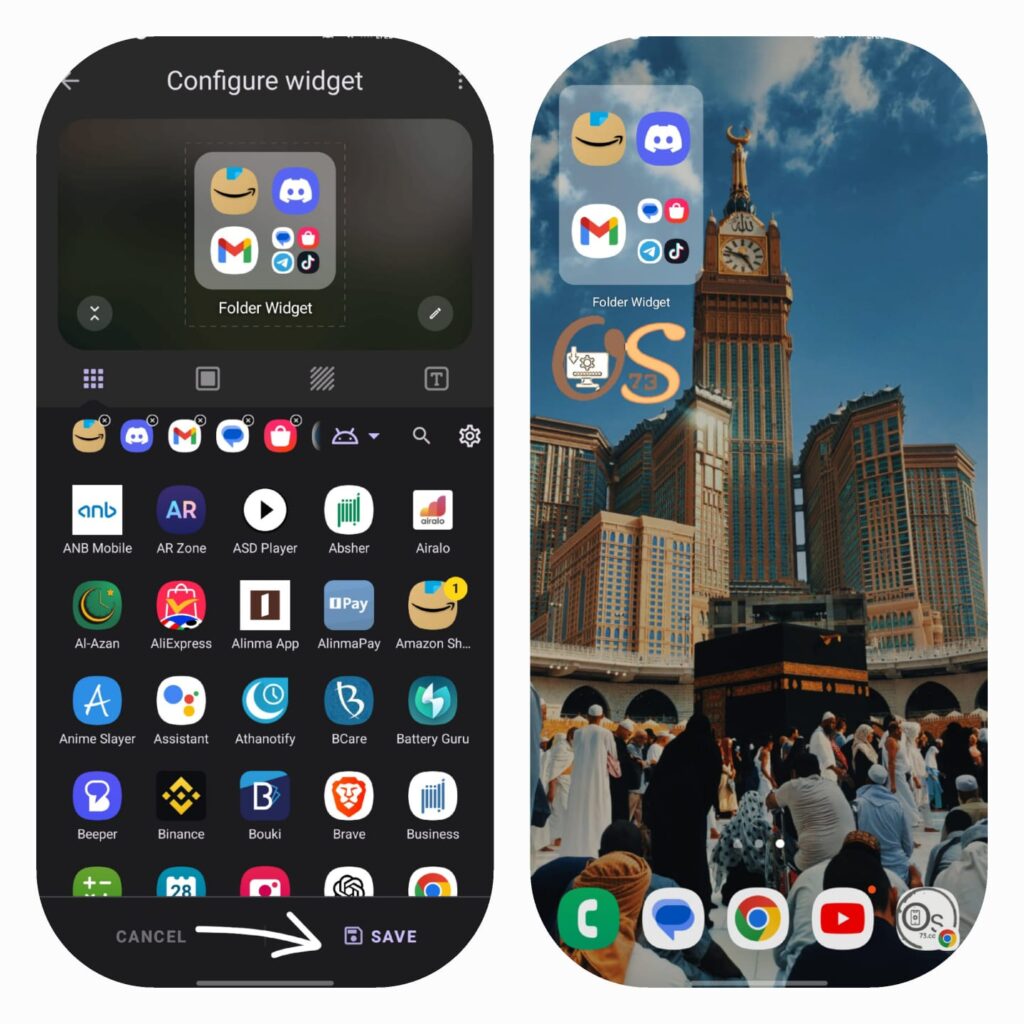
Conclusion:
With the Folder Widget app, you can easily organize your Android phone apps and enhance your phone usage experience. Try the app today and enjoy a neat and attractive phone screen!